Find the Perfect File Transfer Tool
Who are Pro2col?
Every day billions of terabytes are transferred around the world to facilitate our everyday lives - from logistics, order processing, financial transactions to tracking information, and more. Pro2col are a specialist in file transfer and automation workflows which keep the world moving.
Since 2004 we've worked with some of the biggest global brands, helping them to safeguard their data, ensure compliance with regulations and keep their businesses operationally healthy. Employing a consultative approach to solution recommendation, paired with unrivalled Professional Services - you couldn't be in better hands.
Delivering End-to-End
File Transfer Solutions by...

We Help Every Step of Your File Transfer Journey!
Leading Solutions
With experience in a wider range of file transfer software than any other consultancy, Pro2col's experts are uniquely placed to help you choose, and implement, a solution that will transform your business capabilities.

Global Experience
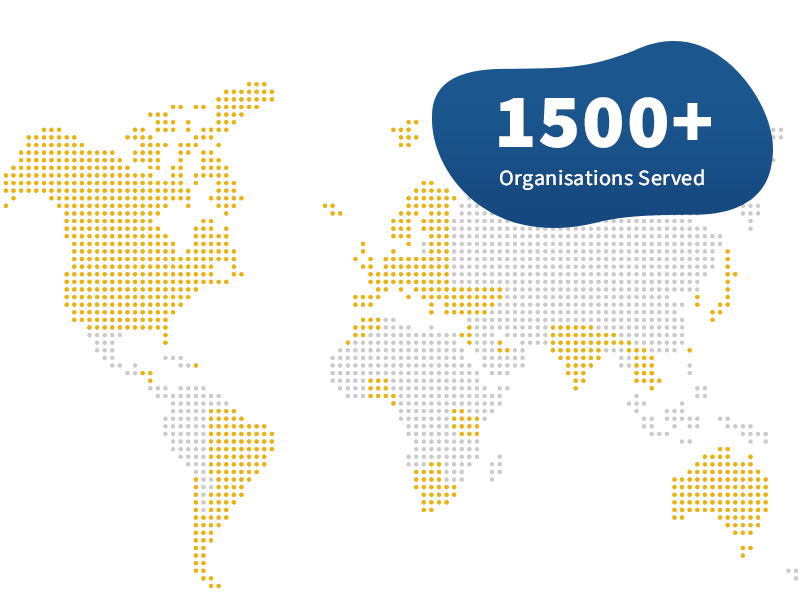
Pro2col have deployed file transfer solutions for some of the largest businesses around the world. Major international banks, retail giants, global logistics companies and national and local governments have all turned to Pro2col for expert advice.
Trusted Services
Our customers rely on the movement of hundreds of millions of files each year. Pro2col offer a Managed Service, Professional Services, Cloud-Hosting and Consultancy Services to keep those files moving smoothly and securely. Need more internal support? We offer training too!

First-Class Support
With more than 72 years' worth of experience working with File Transfer tools our team provides front-line support that is second to none. Our support team are based in the UK and if you have a software issue we'll lend our considerable weight to chasing for a timely solution.
*Data between 11/22 and 11/23
Explore Pro2col
Frequently Asked Questions
All businesses need to transfer data securely. Pro2col specialise in a niche software called managed file transfer (MFT). MFT enables businesses to secure data in transit and at rest, automate transfers between systems, and integrate with different applications.
This supports cybersecurity and compliance and drives business efficiencies. Pro2col is completely independent and has worked with this niche technology since 2004 which allows us to offer clients a purely unbiased, independent and expert review of MFT vendors. Our software experts scope, implement, configure, support and manage MFT solutions for organisations in central and local government, financial services, retail, logistics, healthcare and other industry sectors.
We have a strong understanding of various MFT vendors and solutions available in the managed file transfer market. Customers time and time again value our expertise, insight and recommendations.
At Pro2col we pride ourselves on being vendor-neutral, meaning we don't have exclusive partnerships with specific MFT vendors. This neutrality allows us to provide unbiased recommendations based on our customers’ unique needs and requirements. We assist our clients in finding the best MFT vendor solution for their business through a comprehensive approach:
- Needs Assessment: We start by ensuring we understand our clients’ business requirements, existing infrastructure, and specific file transfer challenges. This involves consultations and assessments to identify pain points and objectives.
- Vendor Analysis: Leveraging our extensive knowledge of the MFT market, we conduct in-depth research on various MFT vendors and solutions. We consider important factors such as security, automation capabilities, scalability, compliance, and budget constraints.
- Customised Recommendations: Based on our experience, assessments and vendor analysis, we provide tailored recommendations to our clients. These recommendations often include a shortlist of MFT vendors that align with the client's needs and objectives.
- Product Demonstrations: We arrange product demonstrations and proofs of concept with the selected MFT vendors. This allows clients to see the solutions in action and evaluate how they meet their specific requirements.
- ROI Analysis: We help clients assess the Return on Investment (ROI) associated with each MFT solution. We consider factors like cost savings, efficiency gains, and risk reduction to demonstrate the potential benefits of each option.
- Pilot Projects: In some cases, we may recommend starting with a pilot project to validate the chosen MFT solution in a real-world environment. This minimises risk and allows for fine-tuning before full implementation.
- Licensing and Procurement: We assist clients with licensing and procurement negotiations, ensuring that they obtain the most favourable terms and pricing from the chosen MFT vendor.
- Implementation Support: Once a vendor is selected, we provide implementation support to ensure a smooth transition. They help configure the MFT solution according to the client's requirements and provide training to staff.
- Ongoing Support: We offer ongoing support and maintenance services to ensure the MFT solution continues to meet the client's evolving needs. This includes troubleshooting, updates, and performance optimisation.
- Knowledge Sharing: At Pro2col we believe in knowledge sharing, in order to provide clients with the necessary training and resources to become self-sufficient in managing their MFT solution.
Having worked in the managed file transfer market since 2004, our expertise in the MFT field ensures that our clients receive a solution that optimally addresses their file transfer challenges and business goals.
SFTP (Secure File Transfer Protocol) and MFT (Managed File Transfer) are both technologies used for transferring files securely, but they serve different purposes and have distinct features and benefits. Let's explore the key differences and the benefits of MFT over SFTP:
Purpose:
SFTP serves primarily as a secure file transfer protocol, offering encryption and authentication for transferring files between systems over a network. It finds common use in ad-hoc file transfers and basic automation but lacks advanced management capabilities.
In contrast, MFT is a comprehensive solution that goes beyond secure file transfer. It is designed to manage, monitor, and govern file transfers within an organization. MFT includes features such as automation, workflow management, tracking, auditing, and reporting.
Security:
- SFTP is renowned for its robust security features, including data encryption during transit and user authentication. It establishes a secure channel for file transfers.
- MFT enhances the security of SFTP by introducing features like granular access control, encryption at rest, and compliance with various security standards and regulations. It offers advanced security management capabilities.
Automation:
- SFTP can be automated to some extent through the use of scripts and scheduled tasks. However, achieving advanced automation often necessitates additional scripting and custom development.
- MFT solutions come equipped with built-in automation capabilities. They facilitate the creation of workflows, scheduling transfers, and triggering actions based on events. This simplifies the process of streamlining and automating file transfers.
Visibility and Monitoring:
- SFTP provides limited visibility into file transfer activities, and monitoring and tracking may require customized solutions.
- MFT solutions offer advanced monitoring and reporting features. They provide real-time visibility into file transfers, generating comprehensive logs and alerts that aid in the identification and resolution of issues.
Scalability:
- SFTP is suitable for transferring files between two systems but may require manual scaling and management when dealing with larger or more complex transfer requirements.
- In contrast, MFT solutions are designed with scalability in mind. They can efficiently handle high volumes of file transfers across multiple systems and often include load balancing and failover capabilities.
Compliance and Governance:
- SFTP, on its own, lacks extensive compliance and governance features. Meeting regulatory requirements may necessitate additional effort and solutions.
- MFT solutions are purpose-built with compliance in mind. They frequently include features for enforcing security policies, tracking compliance, and generating audit reports, simplifying compliance and governance efforts.
Historically, Managed File Transfer (MFT) solutions have evolved to address the limitations of basic file transfer protocols like SFTP. Organizations increasingly require more than just secure file transfer; they need end-to-end visibility, automation, and enhanced security features. MFT solutions have adapted to these needs, providing a centralized platform for managing file transfers across the enterprise.
In summary, while SFTP is suitable for basic secure file transfers, MFT offers a more comprehensive and advanced solution with benefits in terms of security, automation, monitoring, scalability, compliance, and governance. The choice between SFTP and MFT depends on the specific needs and requirements of your organization.
Workflow automation brings huge benefits to business efficiency and staff job satisfaction, whilst supporting security and compliance. It’s typically used for file-based system to system transfers and brings a number of benefits:
- Automating manual, repetitive processes frees up valuable staff time
- Human error is reduced
- Businesses reduce development costs and reliance on custom code
- Trading partners can be onboarded more quickly
- Security is increased, with encrypted delivery protocols and files encrypted at rest
- Dashboards provide real-time visibility into the status of file transfers
- SLA alerts flag failed transfers so you can prevent a breach
- Supports integration with other applications, both on premise or in the cloud, e.g SharePoint, Amazon & Azure
- Supports compliance with regulatory standards such as, GDPR, PCI, SOX and HIPAA.
Encryption is a critical component of Managed File Transfer (MFT) solutions, serving to safeguard sensitive data during transit and storage. Here's why encryption is important in MFT, along with examples and cautions:
Importance of Encryption:
- Data Security: Encryption ensures that data is protected from unauthorized access or interception. It scrambles the data into an unreadable format, which can only be deciphered by authorized parties with the decryption key.
- Compliance: Many industries and regions have stringent data protection regulations that require the encryption of sensitive data. MFT with encryption helps organizations comply with these regulations, such as GDPR, HIPAA, and PCI DSS.
- Data Integrity: Encryption not only secures data but also verifies its integrity. If encrypted data is tampered with during transfer, decryption will fail, alerting users to a potential security breach.
- Confidentiality: MFT encryption ensures the confidentiality of sensitive information. It prevents unauthorized individuals, including hackers and malicious insiders, from accessing sensitive data.
- Protection against Data Loss: Encryption safeguards data even if it's accidentally sent to the wrong recipient or if a storage device is lost or stolen.
Some Encryption Examples:
- SSL/TLS Encryption: Secure Socket Layer (SSL) and Transport Layer Security (TLS) are encryption protocols used to secure data in transit over networks, such as when files are transferred via HTTPS or FTPS.
- PGP (Pretty Good Privacy): PGP is a popular method for encrypting files at rest and in transit. It's commonly used in email encryption and secure file sharing.
- AES (Advanced Encryption Standard): AES is a widely adopted symmetric encryption algorithm used to secure data at rest in MFT solutions. It's known for its robust security.
- SSH (Secure Shell): SSH provides encrypted communication for secure remote access and file transfer. It's used in SFTP (SSH File Transfer Protocol) for secure file transfers.
Challenges & Pitfalls:
- Key Management: Proper key management is crucial. If encryption keys are lost or compromised, it can result in data loss or exposure. Implement strong key management practices to protect keys.
- Performance Impact: Strong encryption can introduce some computational overhead, potentially affecting the speed of data transfer. Organizations should balance security requirements with performance considerations.
- Compatibility: Ensure that the encryption methods and algorithms used in your MFT solution are compatible with the systems and protocols you are communicating with. Compatibility issues can lead to failed transfers or data exposure.
- Regulatory Compliance: Be aware of specific encryption requirements in your industry and region. Non-compliance can result in legal consequences and fines.
- Regular Updates: Keep encryption algorithms and protocols up to date. Over time, older encryption methods may become vulnerable to new attack techniques, so it's important to stay current.
In summary, encryption is vital in Managed File Transfer to secure sensitive data during transit and storage, maintain compliance, and protect against data breaches. However, it should be implemented carefully with proper key management and consideration of performance and compatibility factors.