The Advantages of Using a
Forward and Reverse Proxy
There are many free ways to implement file transfer in an organisation, from using inbuilt FTP daemons on a Unix server, to installing Microsoft IIS or similar and even trying an open source Managed File Transfer (MFT) product.
What these products have in common is that connections are passed directly through to the server. If the server is sited in a DMZ, then connections pass over the external firewall, but all the data and account credentials are stored in the DMZ. Alternatively, if the server is located in the secure “internal” network zone, firewall ports would need to be opened up directly from the internet into this network zone which may violate internal security policies.
Modern MFT solutions approach this problem in one of two ways. Some products are designed to sit inside the DMZ and encrypt data at rest, while storing account credentials in an encrypted database. Firewall rules between the DMZ and internal network are not required except for collection of the data.
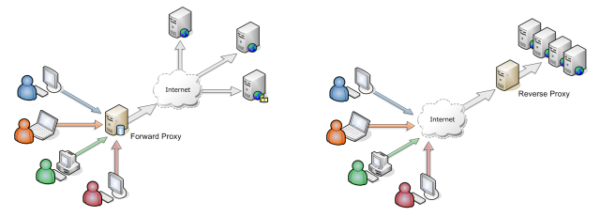
The other which is by far the most popular way, is to use an additional server sited in the DMZ as a forward/reverse proxy server.
A proxy server based in the DMZ, acts as a front end to the MFT solution. Connections are terminated at the proxy and passed back to the MFT server located in the internal network using another/proprietary port. The proxy itself does not store any data or account information but instead acts as an intermediary between the MFT server and the connecting client. This means that if the proxy server were to be compromised by malicious software, no sensitive data is at risk and the attack cannot get any deeper into the network.
Outbound connections from a MFT solution located inside the secure network can also be routed though a proxy. This means that just a single port needs to be opened between the MFT server and the proxy located in the DMZ. For added protection, in most cases this connection is “outbound only” and needs to originate from the MFT server before the proxy responds to any connection attempts. From the proxy out to the internet standard ports can then be used making firewall configurations more straightforward for the network team to configure.
If you implement a proxy server there are also a few added benefits which may not be immediately obvious. Forward Proxies are useful for performing NATing.
Upgrading key solutions like MFT can be a disruptive process and it is not uncommon for Pro2col to come across MFT servers which have not been upgraded for over 5 years as a direct result of the impact and downtime upgrading would have. If a server is using a proxy server, then a new MFT server can be installed next to the out of date MFT server, and at switch over, connect to the proxy server as soon as the old server is taken down. External users and connections see no difference in how they are connecting and downtime appears, from the external connections point of view, to be a few seconds. As a result, upgrade disruption is kept to a minimum, maintenance windows can be scheduled more regularly.
Many organisations have a security policy of data not being stored in the DMZ and using a proxy server can enable the MFT server to stay in the secure part of your network without routing internet traffic though the DMZ to the server.
PCI DSS regulations amongst others stipulate that credit card data cannot be stored in the DMZ, even if it is encrypted. Using a proxy plus the reporting features of MFT enables compliance.
Are you reviewing your data transfer and file sharing processes and systems for GDPR compliance? Pro2col’s GDPR White Paper is an essential read for you.
If you are a little unsure of the best file transfer processes then utilising our Needs Analysis service will really help you get a clear picture of what to do next, what File transfer solutions fit your requirements and what direction you should be heading.
Further Reading:

Do you need help? Pro2col’s expert consultancy will save you time and stress
What is MFT and how does it enhance security, productivity, compliance and visibility? This free guide is compiled from 16+ years’ experience. It includes definition, product features & use cases.
