
Understanding SWIFT CSP Regulation: Key Steps to Business Compliance
Have you ever met an IT manager, administrator, CISO or compliance officer who had a lot of time on their hands? No, me neither. If they exist, then they are certainly a rare breed!
2018 alone, has been a year that has been tough for IT teams.
Between the GDPR, NIS Directive, PCI DSS v3.2.1, the California Data Protection Act and the new SWIFT requirements (no doubt I am missing some). I am not sure there has been a more demanding time for regulatory and industry compliance.
Your teams are without a doubt, under pressure.
To save you time, this blog contains a quick reference to the new SWIFT mandatory Customer Security Programme (CSP) and how you can meet its requirements.
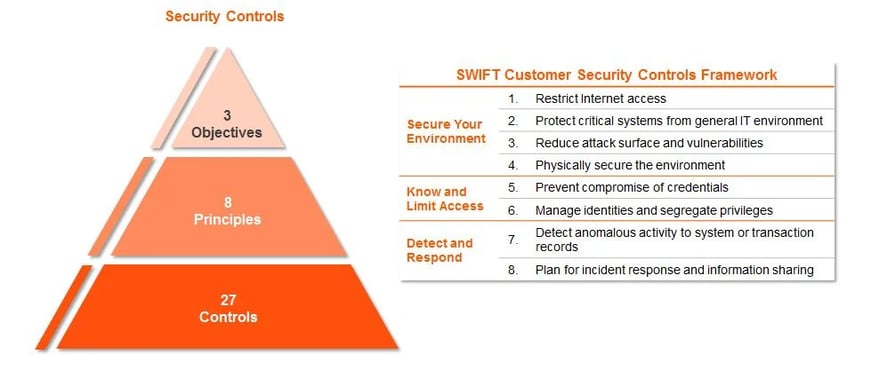
Restrict Internet Access and Protect Critical Systems from General IT Environment
Requirements:
- Any SWIFT infrastructure should be protected from potentially compromised environments or IT equipment.
- Restrict and control accounts which have administrative permissions over applications and operating systems.
Recommendations:
- Prevent direct connection from the internet, VPNs or unrelated elements of the internet to SWIFT infrastructure using firewalls, VLANs or air-gapping.
- Have a documented process for assigning administrative accounts and only assign such accounts to those who have an absolute need as part of their role to possess one.
- Segregate administrative accounts from those which are used on a general day-to-day basis, so that administrative accounts are only used at the point of privilege escalation need.
Reduce Attack Surface and Vulnerabilities
Requirements:
- Ensure secure connections between SWIFT applications and SWIFT operators.
- Reduce vulnerabilities in SWIFT infrastructure and supporting applications.
- Ensure the attack surface of SWIFT infrastructure is kept to a minimum.
Recommendations:
- Use encrypted and validated communications between operators/applications/supporting infrastructure and SWIFT applications. This could be via secure protocols such as those protected with SSL.
- Ensure that there is an update and patching programme which regularly assesses SWIFT infrastructure for vulnerabilities and resolves them.
- Regularly assess SWIFT infrastructure against secure configuration standards such as CIS benchmarks, to ensure they configured to industry recommendations.
An automated tool such as NNT's Change Tracker can compare operating systems, network devices and applications against the CIS benchmarks in minutes. Visit our NNT Change Tracker page for more information.
Physically Secure the Environment
Requirements:
- Prevent unauthorised physical access to SWIFT infrastructure, cloud based locations and workplace environments.
Recommendations:
- Review office and data centre physical security. Examples include, CCTV, locks on doors, locks on data centre equipment cabinets and secured data ports in rooms.
- Review the security of any third-party hosting providers who might be involved in SWIFT infrastructure.
Prevent Compromise of Credentials
Requirements:
- Ensure that passwords are sufficiently strong to prevent password guessing.
- Prevent compromise of weak passwords by using a second factor of authentication.
Recommendations:
- NIST no longer recommends complex passwords or regular changing of passwords, however for the requirements of SWIFT, this should be in place.
- Use a multi-factor authentication solution, whereby a random string of numbers or characters are generated on a device or smartphone, which can be entered alongside a username and password. This means that even if the password is compromised, there is still a restrictive factor.
SecurEnvoy is an award-winning multi-factor authentication solution which can easily be used with applications, network devices and operating systems to secure the authentication channel.
If you would like more information about SecurEnvoy, speak to one of our product specialists today.
Manage Identities and Segregate Privileges
Requirements:
- Enforce least privilege access controls.
- Ensure physica tokens are managed and tracked.
- Protect physically and logically recorded passwords.
Recommendations:
- As mentioned in an earlier recommendation, administrative or accounts with privilege should only be provided to those who have a need as part of their job function.
- Where physical or software multi-factor authentication tokens are used, use a management tool or interface to assign and track the usage of those tokens.
- Passwords should always be stored in an non-clear format so they cannot be read. Where passwords are stored by IT teams, keep them in a password vault or safe storage application.
Detect Anomalous Activity to Systems or Transaction Records
Requirements:
- SWIFT infrastructure is protected against malware.
- SWIFT applications are protected against integrity lessening attacks.
- Database records created by the SWIFT messaging interface have their integrity ensured.
- Security events and anomalous activity in SWIFT infrastructure is monitored and recorded.
Recommendations:
- Use malware detection tools.
- Implement a file integrity monitoring (FIM) solution to detect changes to the environment and database records.
- Use syslog and or other logging solutions to capture security events.
NNT's Change Tracker has both centralised logging and file integrity management capabilities to assist with these requirements; and is trusted by some of the world's most recognisable brands.
Plan for Incident Response and Information Sharing
Requirements:
- Ensure a consistent and effective response for the management of cyber incidents.
- Ensure all staff are aware of their responsibilities and are trained to be "cyber-aware".
Recommendations:
- Thoroughly research and put in place a cyber incident response plan, this should include notification of stakeholders, responsibilities, continued availability and reporting obligations.
- Conduct regular training exercises with staff to ensure their practises adhere to your IT usage policy and SWIFTs expectations.
Our preferred partner and widely respected advisory organisation Cyber Management Alliance offers cyber incident response and planning training to organisations globally. Their programme is highly regarded and worth looking into.
|

