 Pro2col finally saw the anticipated increase in demand for hybrid managed file transfer (MFT) infrastructure in 2020. Will 2021 be its coming of age?
Pro2col finally saw the anticipated increase in demand for hybrid managed file transfer (MFT) infrastructure in 2020. Will 2021 be its coming of age?
File Sharing and Secure Email
WHAT IS FILE SHARING AND SECURE EMAIL?
Secure File Sharing is a term used to describe sending files with sensitive data securely, whilst being able to collaborate both internally and externally. Gartner call it “content collaboration”, and it’s also known as “file sync and share” or “EFSS”.
Secure file sharing enables organisations to secure files and data at all stages, in transit, at rest and in storage whilst maintaining ease of collaboration for employees or external partners.
With compliance standards such as GDPR to follow, secure file sharing keeps your data secure but crucially auditable. Therefore, you always have control and a log of what data is where and who it has been accessed by.
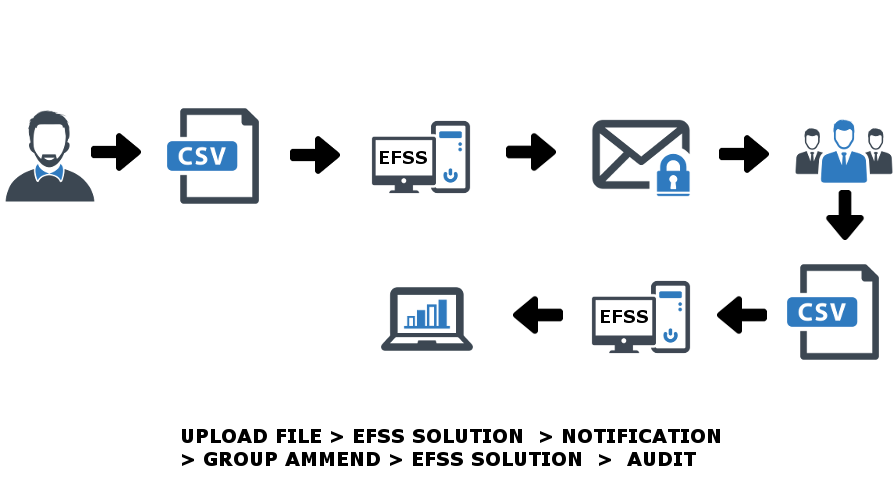
Secure email is a term used to describe a way to send a file to someone in a safe and efficient manner. The terms “ad hoc” or “person to person” are also sometimes used.
A secure email solution will quite simply allow you to create a single job, enter the email address of your recipient, add a download link and press send. That’s it. No further details concerning your recipient are required and all they need in order to receive the file is a standard email account, you can make this even more secure if you wish.
Secure email file transfer is typically implemented by businesses that need to gain greater visibility of files leaving and entering the organisation. More often than not they’re implemented to replace consumer-grade solutions like Dropbox, WeTransfer or other consumer cloud based systems.

Businesses and in particular IT or data protection officers are continually looking to ensure the security of an organisations data and files. With employees needing to send information to partners or fellow colleagues file sharing and secure email solutions can eliminate a lot of their worries:

Organisations are typically looking to:
- Enable timely file sending for employees
- Have better visibility of files sent and who has accessed and downloaded the information
- Send files faster and in a controlled way
- Eliminate the worry of large files being able to be sent
- Secure sensitive information so it’s not lost or hacked
- Enable safe document collaboration internally and externally
- Enable remote working or remote access to files via mobile
- Abide by compliance standards such as GDPR
- Make documents signable
IT often looks to file sharing and secure email to:
- Add to existing office 365, MS Exchange, or Google email servers, for ease of use for employees
- Remove the single point of failure of homegrown bespoke file transfer solutions
- Replace consumer-grade file sharing such as Dropbox or WeTransfer
- Have control and be able to audit the sending of files and data
- Set expiry and maximum downloads on files to keep control
- Transfer files across a secure HTTPS connection
- Integrate with other applications and systems
- File share on a cloud infrastructure

Whether you have technical expertise or not, your business can utilise file sharing and secure email easily. You can purchase and host onsite or we can help you host the solution in your cloud environment.
File sharing and secure email solutions can integrate and work in conjunction with the following applications:





Our expertise makes us the preferred partner for many of the leading file Sharing and secure email solutions. We provide software licences, professional services and support for all of these recommended solutions. Some are pure file sharing and secure email solutions, while others offer this feature as part of a managed file transfer solution:
3 Powerful Examples of MFT and DLP Paired in Action
Sep 10, 2020 | Blog , Secure File Transfer , Managed File Transfer , Pro2col
 Using a DLP MFT combination, you can extend security, whilst minimising disruption to business processes and workflows.
Using a DLP MFT combination, you can extend security, whilst minimising disruption to business processes and workflows.
Backing up Cisco Unified Communications Manager through SFTP
Feb 24, 2020 | Blog , Secure File Transfer
 Here we explain the process of backing up your Cisco Unified Communications Manager (CUCM) using an SFTP server. This can be applied to any SFTP server.
Here we explain the process of backing up your Cisco Unified Communications Manager (CUCM) using an SFTP server. This can be applied to any SFTP server.









