Secure Online Forms and Automation
A secure, customisable method for submitting information
Businesses need information from their internal users, external customers and suppliers all the time and it is highly likely this will include personal or sensitive data.
It is definitely not appropriate to ask users to share this information over email, but we know that is still common practice for many organisations. Email is not secure, so you’re risking compliance, plus there is no guarantee of delivery. Email cannot support large files either.
Online forms provide a secure, customisable mechanism for your customers, suppliers and internal users to submit information to your business. It is a popular feature of Managed File Transfer systems and can capture any type of information or file size. Fields can also be configured to trigger onward business processes or integrate with internal systems.
To demonstrate the versatility and functionality of secure online forms with automation, let’s look at a use case from the motor insurance industry.
Use case: Motor insurance company
A customer is involved in a collision and needs to claim on their insurance. Using the secure online form, they enter the information required: Policy number, personal details, vehicle information, details of the collision and images of the damage.
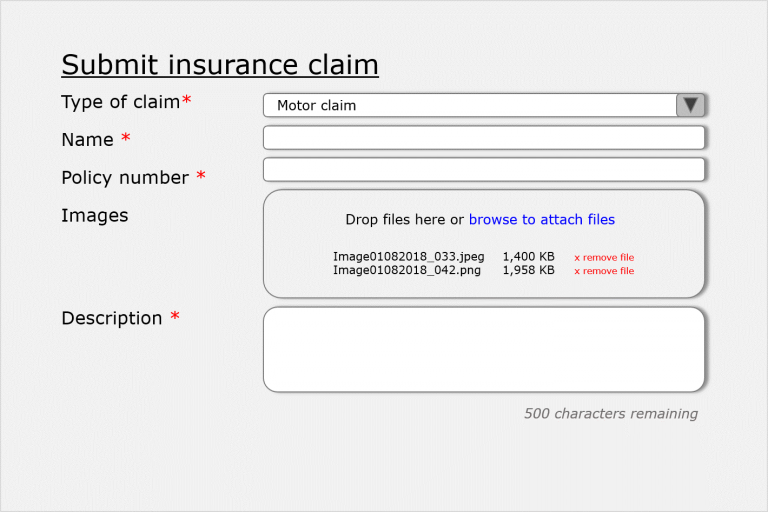
Once the data has been received, a number of tasks need to happen to progress the claim.
This is where the technology really comes into its own. Automated actions sitting behind the secure online form, can execute many of these tasks and you can find out more in this video.
Examples of automated workflows
Once the user submits the form, it can trigger a range of automated workflows, such as:
- Validate customer name against policy number
- Check the policy number meets alphanumeric sequence
- Assign claim to claims handler
- Automatically input the description directly into the customer database
- Rename images to a pre-determined format, e.g.: policynumber_date
- Move images to the image server
- Send an automated reply via email or SMS, or other business communication platform. The template can be personalised to include the name, assigned claims handler, policy number etc.

Software:

Tools:

All of these processes can take place without any human intervention, demonstrating just how more efficient these labour-intensive tasks can become. You can see how this would suit other industries, such as mortgage brokers, doctors and private healthcare providers, or any outsourced business service, such as HR or payroll.
Use case: Local authorities
Local authorities need information from their residents, staff and suppliers all the time, and these records are highly likely to include personal or sensitive information.
It is definitely not appropriate to ask users to share this information over email, but it’s still common practice. Email is not secure, which means risking a GDPR breach, plus there is no guarantee of delivery. Furthermore, email cannot support the transfer of large files.
Online forms provide a secure, customisable mechanism for users to submit information. They are a popular feature of managed file transfer systems, because they can capture any type of information, including files of any size. Fields can also be configured to trigger onward processes, or integrate with other systems.
To demonstrate the versatility and functionality of secure online forms with automation, let’s look at some use cases.
- Use case #1: Reporting incidents
When a local resident wants to report an incident such as potholes, vandalism, litter, or drug use, secure forms can be used to capture the data and automate onward processing. To begin with, the secure form is capable of matching the location of the incident to the local authority’s jurisdiction. The form can also capture images, of any file size, and then automatically move them to a defined file location. Integration with other in-house systems also allows incidents to be assigned to the relevant team, or for automated responses about the progression of the report to be sent. - Use case #2: Adult and child social care – reporting concerns
In this scenario, any data relating to the reporter, or the subject, is highly sensitive so security is critical. Capturing this data in a secure form enables it to be automatically and securely moved to the correct file location. In addition, alerts could be set to notify the relevant team member based on keywords in the submission. A human action can be inserted at any point in the automation sequence. For example, once the form has been submitted and data distributed to the correct file locations, a human action can be set for an employee to review the submission and categorise the report in terms of urgency, refined locality, or severity. Alternatively, or once this human action is complete, the report can be automatically assigned to a case handler, or a call-out can be automatically set up. - Use case #3: Community transport and parking permits
A secure form can automate the booking process for community transport by capturing user data and matching it against a database. This ensures that bookings are recorded and remaining spaces are updated accordingly in real-time, maintaining the accuracy of availability information. Users’ eligibility can also be checked by validating a postcode against a database of accepted locations. In the case of parking permits, uploaded files of car ownership and insurance documentation can be submitted and matched against each other. When a match is identified, an action to grant the permit can be automatically triggered, freeing up employees’ time to focus on other tasks.
These are fairly simple use-cases, but there’s no end to the automation capabilities that can be applied. We recently customised secure online forms for a company sequencing hundreds of thousands of anonymised records of biological data. Customised logic built around metadata in mandatory fields in the form triggered the next step in the process.
Can you see how your organisation could benefit from using secure online forms? Get in touch now.

Take the risk out of selecting an MFT solution with our free, independent comparison service!
Our comparison report identifies the right solution for your needs and budget. Complete a series of questions and receive a bespoke product recommendation from our technical experts.