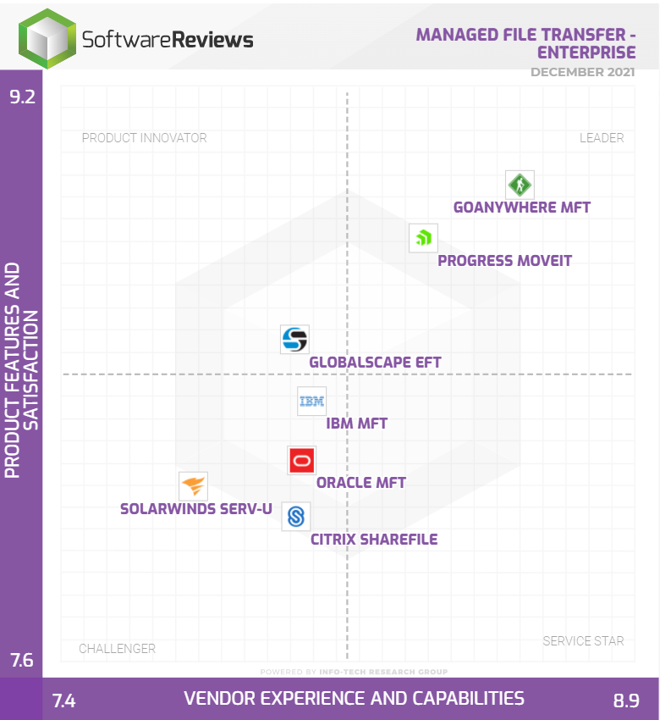
 As 2021 draws to a close, Software Reviews have released their latest Info-Tech MFT Data Quadrant. Regular readers of this blog will remember we highlighted concerns about the 2019 report – namely that several of the featured products weren’t actually managed file transfer (see our full 2019 review below ).So, what does the 2021 report look like, and is it a more accurate reflection of the marketplace?
As 2021 draws to a close, Software Reviews have released their latest Info-Tech MFT Data Quadrant. Regular readers of this blog will remember we highlighted concerns about the 2019 report – namely that several of the featured products weren’t actually managed file transfer (see our full 2019 review below ).So, what does the 2021 report look like, and is it a more accurate reflection of the marketplace?
Secure File Transfer
Secure file transfer. There are several ways to send and receive files via a web browser, client to server and email. Secure file transfer includes a variety of security protocols to secure the communication channels.
-
-
-
- Chapter 1: What is Secure File Transfer?
- Chapter 2: Secure File Transfer Solutions
- Chapter 3: Secure File Transfer Resources
- Chapter 4: Secure File Transfer Use Cases
- Chapter 5: The Latest Secure File Transfer Related Tips and News
- Chapter 6: Discuss Secure File Transfer With An Expert
-
-
Introduction to secure file transfer
If you’re reading this page you’ve probably found or been introduced to the term secure file transfer and want to find out more. Congratulations – you’re in the right place. You may want to find out which protocols to use or how you can share information securely with partners or customers. Here you will learn about secure file transfer and how the different technology solutions address different requirements. Of course, if you don’t find the answer you are looking for you can always ask us. To make sure you’re not wasting your time, let’s start by defining secure file transfer. Then you can be sure the following information will be relevant.

Chapter 1:
What is secure file transfer?Files are typically sent using HTTP (via a web browser), FTP (client to server) or email. Secure file transfer is when files are transferred using a security protocol to secure that communication channel.
This is incredibly important in corporate environments because organisations are regularly handling personal and sensitive data. Laws like the GDPR and industry standards such as PCI DSS, Sarbanes Oxley and HIPAA dictate an organisation’s responsibility to secure this data. As such, secure file transfer solutions have become a priority for all businesses.
The protocols vary depending on how the file is being sent and received. The key secure file transfer protocols include:
- FTPS (FTP run over SSL/TLS)
- HTTPS
- SFTP (SSH – Secure Shell protocol)
When using the FTPS and HTTPS file transfer protocols, files are sent over a TCP connection. This TCP connection has a TLS (transport layer security) or SSL (secure socket layer) security layer that runs beneath the FTP and HTTP protocols. SSL is a protocol that establishes an agreement between a client/browser and a server. The sending side uses a public key to encrypt a data file, which is then sent using either the FTP or HTTP file transfer protocol. The receiving side will have, as part of the agreement, a unique private key that can decrypt the data file.
SFTP is not just FTP run over SSH. It is a stand alone, dedicated secure file transfer protocol. The file transfer protocol itself does not provide authentication and security; it expects the underlying protocol (SSH) to secure this. SSH is used to establish a connection between a client and server that acts like an encrypted tunnel. This encrypted tunnel protects any data files that are sent via this secure connection.
Different types of technology deliver secure file transfer. The right solution for you will depend on how you are transferring data and the level of functionality you require.
Here are some of the solutions that can address your secure file transfer needs. Click on the solution to find out more.
File sharing & secure email
Managed File Transfer
Automated file transfer
Cloud MFT
Chapter 3:
Resources to help you research secure file transferSecure online forms & automation
Businesses need information from their internal users, external customers and suppliers all the time and it is highly likely this will include personal or sensitive data. Secure online forms capture this data and deliver onward processes securely.
Managed File Transfer comparison
This solution comparison service asks all the right questions about your secure file transfer requirements. Just complete the questionnaire and our independent experts will review your answers and recommend the best fit for you.
These case studies are just some examples of how different industries have addressed their secure file transfer requirements.
Professional services
A professional services company decided to outsource a particularly large area of its operations: Finance. But without an effective electronic solution, the only way to transfer data to their external provider was to send forms through the post and scan them. This was a time consuming manual process. And with financial data often forming the basis for decisions across the entire business, the data needed to be up to date. Out of date information could have disastrous consequences.
The company implemented a Managed File Transfer solution. This allowed them to securely, quickly and seamlessly move data out to external suppliers for processing, then back into the business.
Public Sector
A local council used Managed File Transfer to move information to third-parties when it couldn’t securely connect via existing government gateways. Files were sensitive, such as reports concerning a member of the public, or a contractual negotiation with a supplier.
Secondly, the solution was used by anyone wishing to send information to the council. Similar to a self-addressed envelope, a council employee could simply send an empty package to the third party, in which they place their documentation before pushing it back securely.
Finally, because users often prefer MFT to email, it was used for the simple and rapid transfer of very large or numerous files to suppliers.

Insurance
Insurance companies need information from their internal users, external customers and suppliers all the time and it is highly likely this will include personal or sensitive data.
It is definitely not appropriate to ask users to share this information over email, but we know that is still common practice for many organisations. Email is not secure, so you risk a breach of the General Data Protection Regulation (GDPR), plus there is no guarantee of delivery. Email cannot support large files either.
Online forms provide a secure, customisable mechanism for your customers, suppliers and internal users to submit information to your business. It is a popular feature of Managed File Transfer systems and can capture any type of information or file size. Fields can also be configured to trigger onward business processes or integrate with internal systems.

Retail
Many MFT solutions have built-in settings to help an organisation configure their systems to be PCI compliant. Reports can be set to check the configuration of the application meets requirements. Whenever a setting is changed in the application that would breach PCI guidelines, it will ask for a reason for the change. This will then be displayed in the compliance report.
By moving data to and from stores and POS systems on an automated schedule, all data can be stored centrally at head office. This provides a better picture of how each branch is performing and adds another layer of security to the data. This automation can also be used to trigger orders when stock levels get low.

NHS and the healthcare industry
A medical company wanted to eliminate their reliance on multiple file integration protocols. These were owned by their former parent company. Rather than duplicate the existing complicated systems, they installed Managed File Transfer. This simplified and managed their automated and manual data transfers, whilst providing greater control and a more secure, reliable flow of data. This was particularly important for financial information such as invoices, orders and Bankers’ Automated Clearing Services (BACs) files. Managed File Transfer reduced their reliance on multiple solutions and offered a range of other secure file transfer, automation and reporting functionality.

Managed File Transfer software comparison
Oct 14, 2021 | Blog , Automated File Transfer
 Start your Managed File Transfer software comparison. Answer a series of questions about your business requirements. We’ll compare how the different solutions meet your needs and make a free recommendation.
Start your Managed File Transfer software comparison. Answer a series of questions about your business requirements. We’ll compare how the different solutions meet your needs and make a free recommendation.
Solarwinds Serv-U MFT Server review
Sep 25, 2023 | Blog , Managed File Transfer , Pro2col
 We review Solarwinds Serv-U MFT Server and ask the question is it actually MFT and should it be seen as a leader in the market?
We review Solarwinds Serv-U MFT Server and ask the question is it actually MFT and should it be seen as a leader in the market?
Contact Us
We're always happy to help - however big or small your querySimply call or email us and one of our system integration specialists will be in touch to discuss your requirements or queries.
 0333 123 1240
0333 123 1240
 info@pro2colgroup.com
info@pro2colgroup.com
FAQ's
The basics
What is secure file transfer?
There are several ways to send and receive files (via a web browser, client to server and email). Secure file transfer is when files are transferred using a security protocol to secure the communications channel. The protocols vary depending on how the file is being sent/received.
How do I transfer file securely?
There are several different ways to send and receive files, including HTTP (via a web browser), FTP (client to server) and email.
A variety of security protocols can be used to secure the communication channels, depending on how you are transferring it:
- FTPS (FTP run over SSL/TLS)
- HTTPS
- SFTP (SSH – Secure Shell protocol)
Do I need secure file transfer?
Secure file transfer is incredibly important in today’s corporate environments because organisations are regularly handling personal and sensitive data. Laws like the GDPR and industry standards such as PCI DSS, Sarbanes Oxley and HIPAA dictate an organisation’s responsibility to secure this data. As such, secure file transfer solutions have become a priority for all businesses.
Which are secure file transfer protocols?
Secure file transfer protocols vary depending on how the file is being sent/received. The key secure file transfer protocols include:
- FTPS (FTP run over SSL/TLS)
- HTTPS
- SFTP (SSH – Secure Shell protocol)